Blog
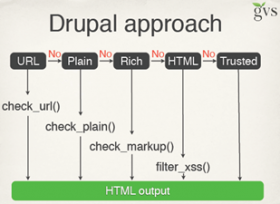
A3 XSS (Cross Site Scripting)
XSS flaws occur whenever an application takes untrusted data and sends it to a web browser without proper validation or escaping. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.

The solution: use Drupal and secure it.
a) Drupal vs OWASP Top Ten

vulnerabilities and threats. CMS Security should be addressed.
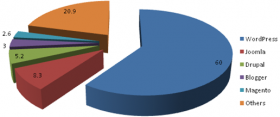
CMS Solutions
According to [1], the top three used product are: WordPress, Joomla! and Drupal. Everyone of these has proper pros and cons. The following graph depicts CMS usage during 2014, according to WebcomWebsites (http://www.webcomwebsites.co.uk/our-articles/ ):
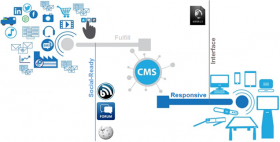
The term “Web 2.0”refers to evolved web techniques such as provide a better interaction between user and site.
This should be performed by the means of a CMS (Content Management System). It allows for websites based
on contents/comments paradigm.
Web 2.0 Architecture
The CMS is an infrastructural layer, offering the following advantages:
· Interface: the user choose the information (text, images, videos) to display, interacting with the website,
according to specific actions (e.g. click, sting insertion).